Respected Enterprises Value Our Work
Privacy Matters, Defenzelite Delivers!
Learn how we keep your business safe: Our Approach to Enterprise Security
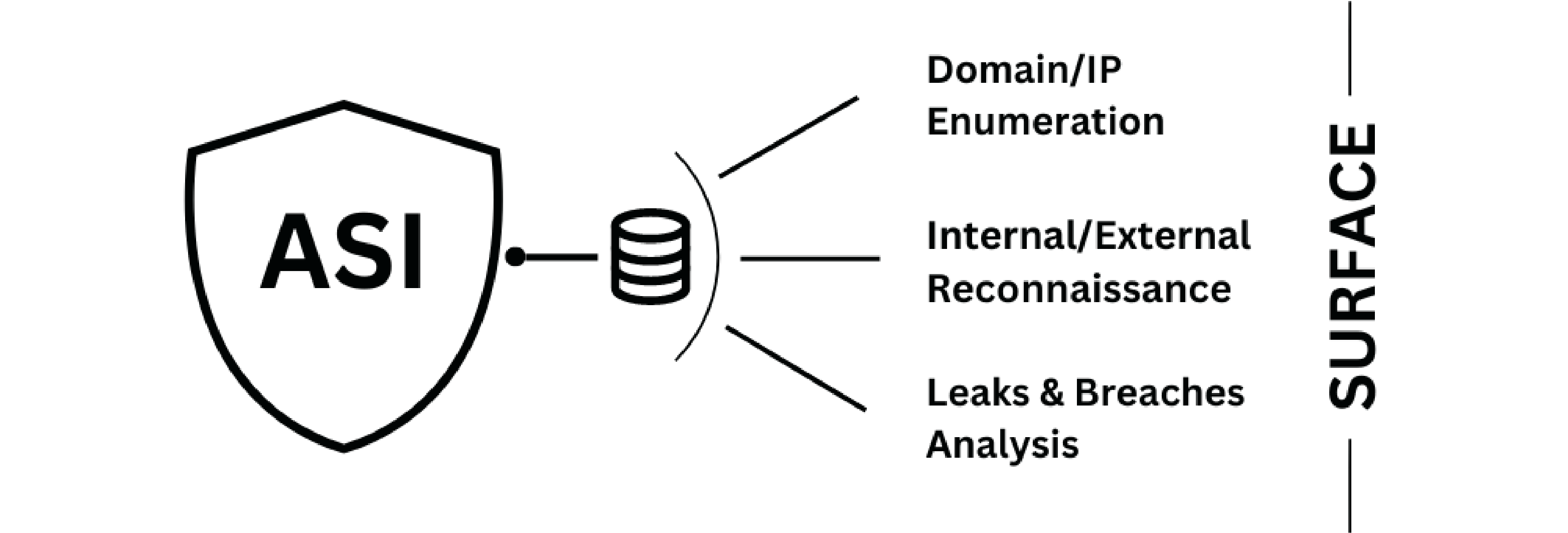
Identifying target attack surfaces with advanced OSINT and information gathering techniques.
Constantly assess & reduce vulnerability across digital systems via Attack Surface Intelligence. Monitoring, data gathering & analysis help identify adversary entry points. Strengthen cybersecurity by understanding weaknesses like misconfigurations & exposed assets.
- Enhanced Defense: Identify weak points to bolster cybersecurity.
- Proactive Threat Detection: Pinpoint adversary entryways for preemptive action.
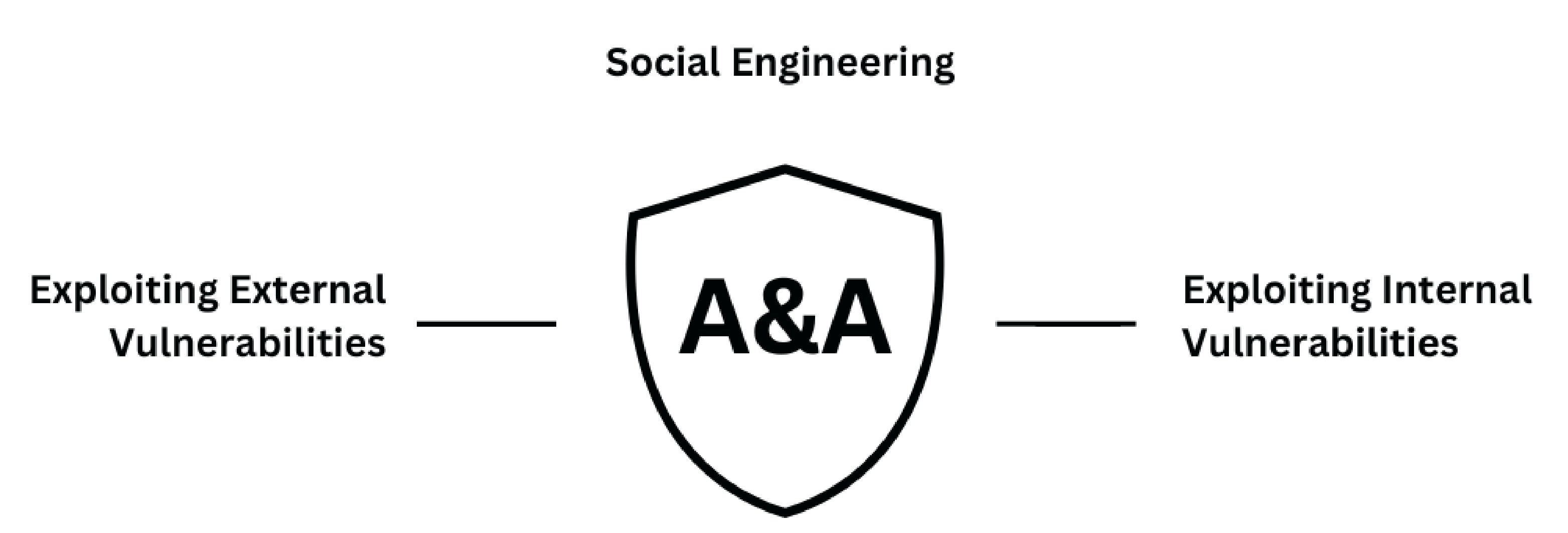
Discovering Hidden Weaknesses
Using Latest Threats and Injection Techniques.
It is a careful way to find and fix security flaws in systems or apps. It involves examining the software, hardware, and processes for weak spots that hackers could exploit. This way, we prevent unauthorised access or data breaches and improve cybersecurity. We do this by using advanced tools and techniques.
- It reduces the risk of financial losses, reputational damage, or legal consequences due to cyberattacks.
- It helps protect the privacy and integrity of data and information stored or transmitted by systems or apps.
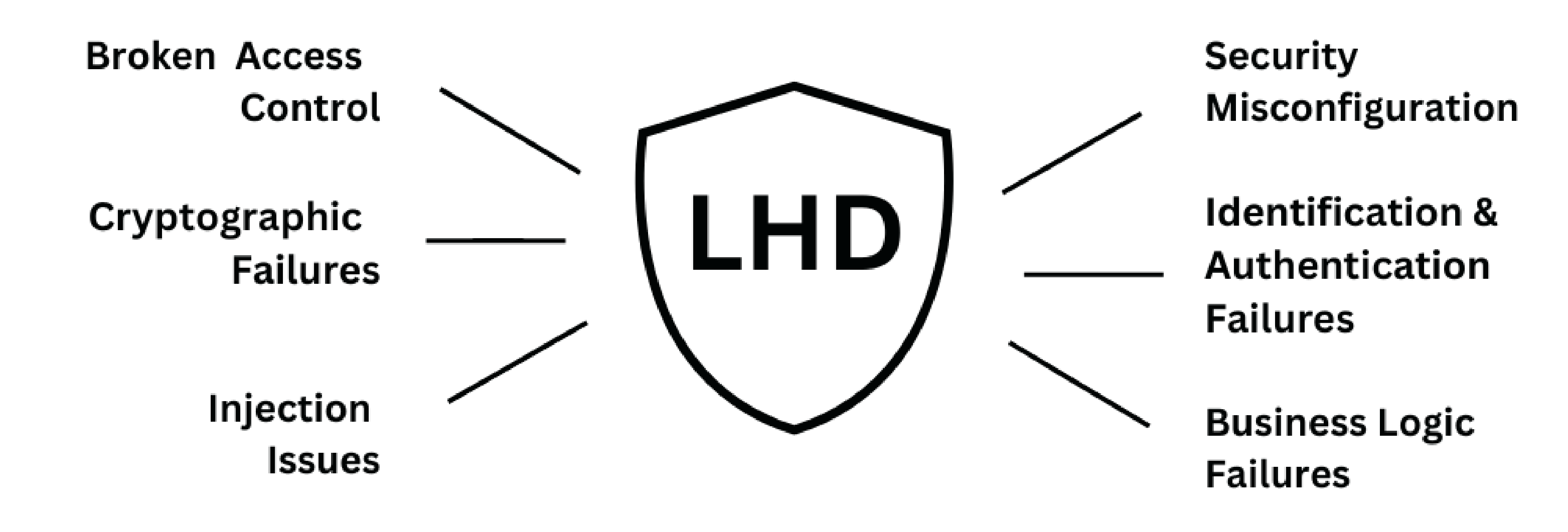
Comprehensive security assessments and audits for your web and apps, covering all the common attack vectors and best practices.
Security Assessment and Auditing are vital for business because they can help you secure your web and apps from cyber threats. By fixing the vulnerabilities and risks, you can avoid data breaches, reputation damage, and revenue loss. By complying with the legal and regulatory standards, you can prevent fines, penalties, and lawsuits. By enhancing your security posture and resilience, you can increase your customer trust and loyalty.
- It help to discover and exploit the vulnerabilities in your applications and IT networks before hackers do
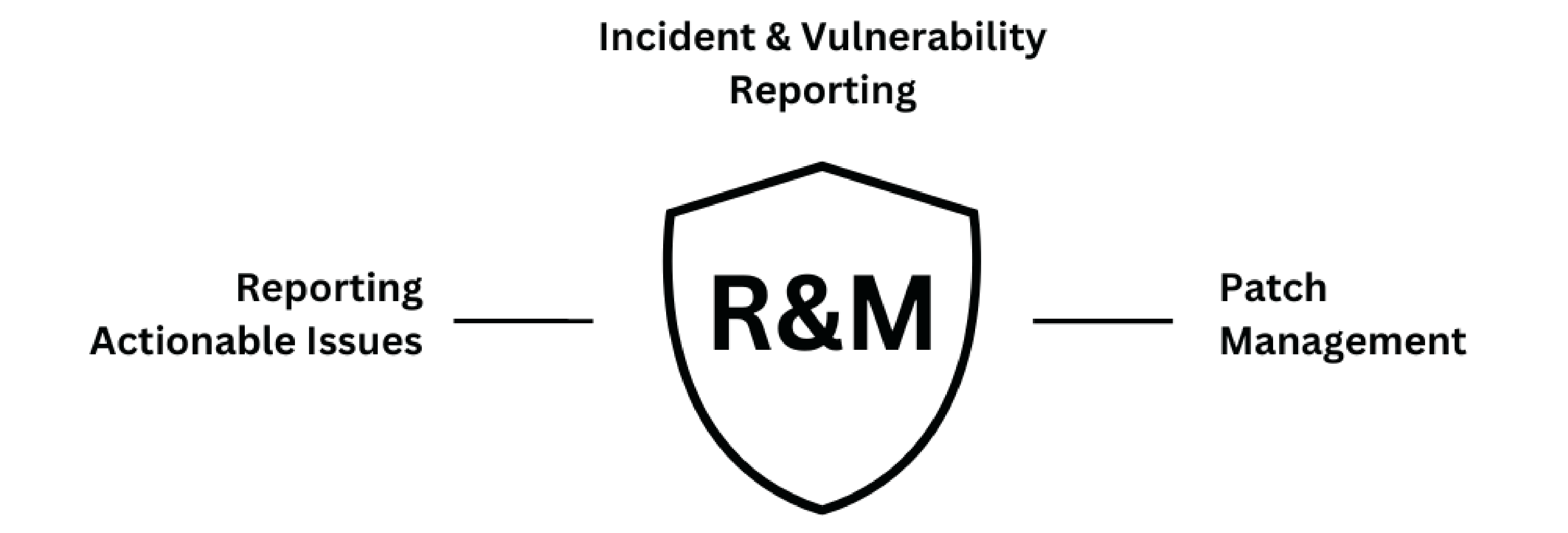
Actionable reporting and rapid mitigation techniques to deal with cyber challenges
Discover the ultimate solution to your business's cyber challenges with our Actionable Reporting and Rapid Mitigation Techniques. Safeguard your digital assets using easy-to-implement strategies. Don't let cyber challenges hinder your growth – equip yourself with the tools to mitigate them swiftly and effectively.
- Quick mitigation helps prevent disruptions that could otherwise affect your productivity and revenue.